Payment security is one of the most critical issues of e-commerce. Account thefts and payment frauds are on the rise on online trading platforms. Therefore, safety and security have become the top concern of customers and an indispensable requirement for e-commerce and retail businesses.
Around the world, many severe cases related to payment fraud and cyber-attacks have taken place. The role of payment security solutions for the information security of the entire commercial application system is significant. Here are ten specific suitable solutions that developers of e-commerce systems should keep in mind.
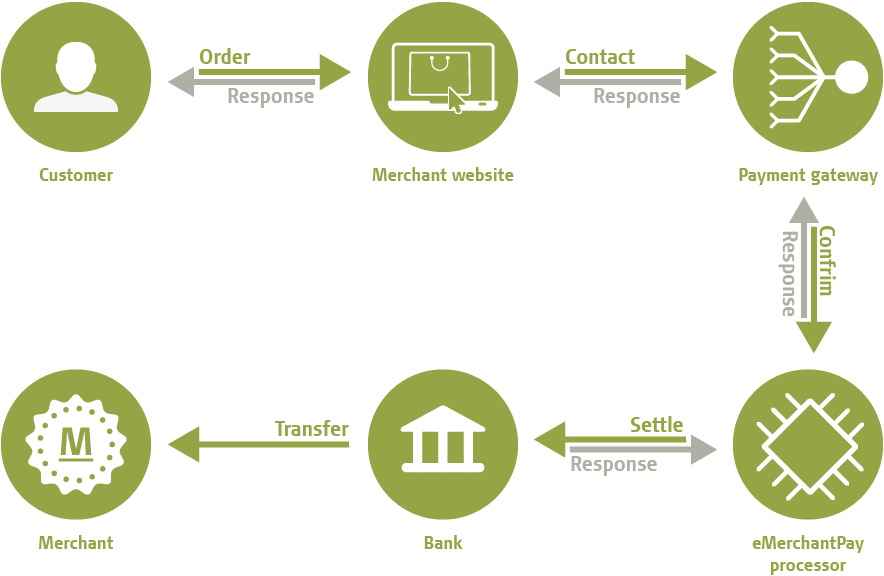
- Partner With A Processor Who Knows Online Payments
Choosing the right payment processor is a prior step for accepting online payments from the customers through credit card. Selection of payment processing partner should be done with utmost care as its experience can help the client to comply with the payment card industry data security standards (PCI DSS).
All you need is an experienced partner who can give you all-time support and maintains the PCI compliance for you by implementing various approaches like a training program, Vulnerability Assessment, and full-time customer support. Some processors even reimburse the money for monetary loss in case of fraud event that occurs through a data breach.
Thus, it is extremely important to have a partner who had experience and can even understand everything about the payment security and precautions.
- Monitored Suspicious Purchasing Activity
E-commerce businesses should be aware of the various types of suspicious activities that could be the reason for fraud.
There was once a case of loss from a suspicious transaction for a fashion business. At that time, customers logged into a website from the same IP address and made huge order but used different credit cards. This is a sign of theft and illegal credit card use. However – the store owner was completely unaware of the issue and thus failed to understand the behavior and pattern of the customer indicated that single person is using multiple stolen credit cards to make purchases which lead to serious repercussion.
Large order raises too many doubts and especially the one which was requested for next day Shipping. But this activity alone is not enough to identify a transaction as fraud.
- Address Verification System For All Transaction
It is extremely important for store owners to predict and analyze that the person making the purchase is truly a cardholder. Various techniques can be utilized to prevent this fraud. Implementing the address verification system in the eCommerce store is the best way to analyze and verify the fraud.
The system will check if the billing address is correct by verifying it with cardholder’s data from the issuing bank. As a result, person with a stolen card or card number doesn’t have the access to the wrong billing address.
Incorrect billing address may not necessarily mean that the transaction is fraudulent hence it is advisable to take additional security measures to identify the customer.
- The Encryption Approach
Encryption is a method of converting the original message into encrypted text, which should be too complex to understand and even difficult for a hacker to decode. The main idea of encryption is to ensure security and safety of the data and its transmission.
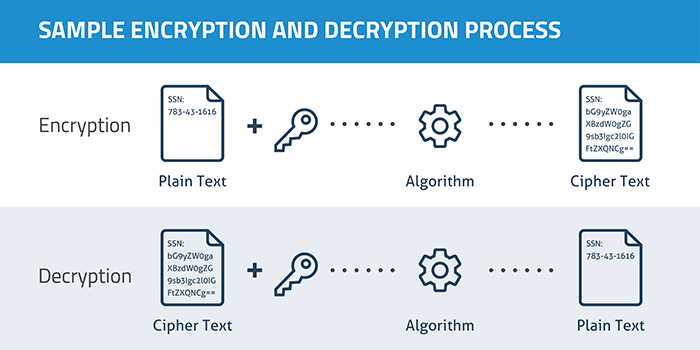
Encryption can be done through various techniques, but the choice totally depends on the context and the requirements. Some of the famous techniques in eCommerce are:
- Public key encryption
- Symmetric key encryption
- Secure Socket Layer (SSL)
Secure socket layer is the most consistent security model used and developed for eCommerce business, secured through its payment channel.
Through the SSL, transmission of data is encrypted, client and server information are authenticated and message integrity for TCP/IP connections. The protocol is design to prevent tampering of information and forgery while transmitting data over the internet between interacting applications.
- Secure Hypertext Transfer Protocol (S-HTTP)
S-HTTP is an advanced version of normal HTTP internet protocol with enhanced security which ensures secure authentication, public key encryption and digital signatures.
Secure HTTP enabled website makes the transaction more secure by negotiating encryptions schemes used between a server and the clients. It can seamlessly integrate with the HTTP and ensure an optimal end-user security with different defense mechanisms.
- Secure Electronic Transaction (SET)
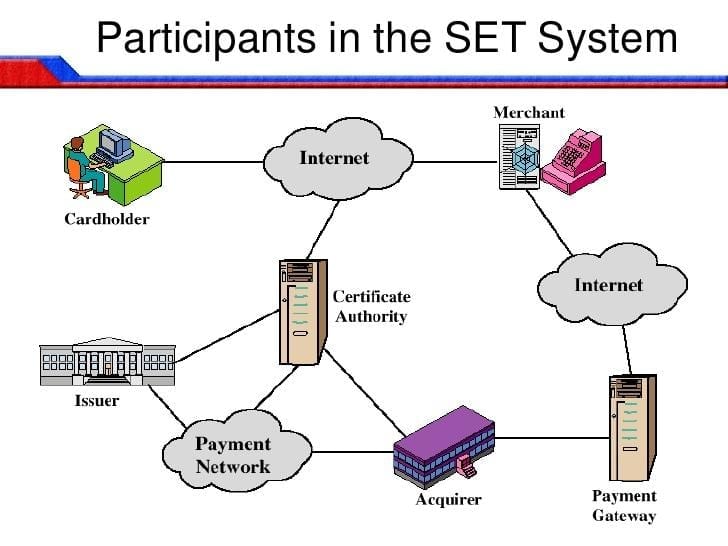
SET is a joint collaboration by MasterCard and VISA which ensures that safety of all parties involved in electronic payments of an eCommerce transaction. It is designed to handle complex and critical functions like:
Authenticating the cardholders and merchants
Confidentiality of information and payment data
Define protocols & electronic security service, providers
- Payment Card Industry (PCI) Compliance
The payment card industry security standard council was formed in the year 2006. It ensures that the companies who deal with the accepting, processing, storing, and transmitting credit card information must maintain a secure environment.
PCI DSS is not a law in itself but a standard made by a collaboration of various branded card company like Visa, Mastercard, JCB, AMEX and Discover. If your company is not PCI compliant has to face some serious consequences like fines, card replacement cost, costly forensic audits and off-course lost to brand image.
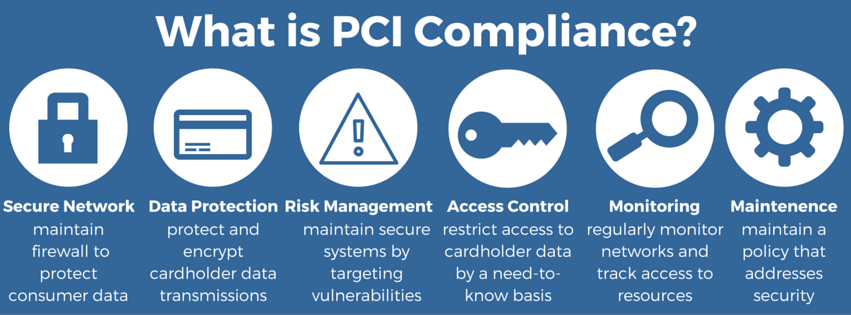
Image Source: cybersecon
As it is said Wise man must always be proactive than reactive because little upfront effort and cost is required to reduce your risk from serious consequences.
- Safe Login Screen
Development of Secure eCommerce website straight away starts from the Login Page. You are halfway done if login access to the website is secure. Otherwise, it will be easy for the hackers to infiltrate and get access to sensitive data.
Implementing this safety protocol is moderately easy, but it can efficiently ward off many security threats.
- Digital Signature
A digital signature means giving a unique identity to your message. Actually, it is a process of encrypting the message with the private specifically used for verification purpose.
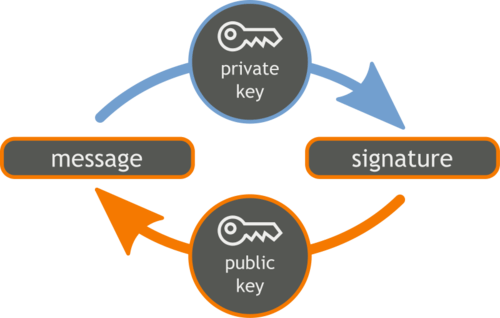
The linkage between data and the signature doesn’t allow any alteration and if anyhow data is altered signature is automatically invalidated.
Thus, digital signature helps to maintain the authority and confidentiality of the data.
Source: cystack.net

 EN
EN